In the realm of cybersecurity, malicious actors are constantly devising innovative read more methods to bypass security protocols. System bypass strategies, therefore, represent a critical area of concern. These techniques enable unauthorized access to protected systems. Understanding these strategies is essential for both defenders and those seeki
A Review Of lizardfolk 5e player race
whilst there aren’t subspecies of Aasimar therefore, some Aasimar do discover on their own in differing circumstances and can be categorised based upon these situation as the next: in the sport’s 50-year background to incorporate rules for taking part in as orcs, Along with the fifth edition mechanics for playing them Earlier relegated to you
 Michael Bower Then & Now!
Michael Bower Then & Now!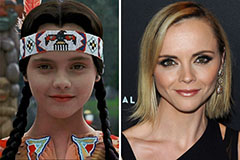 Christina Ricci Then & Now!
Christina Ricci Then & Now! Erik von Detten Then & Now!
Erik von Detten Then & Now! Raquel Welch Then & Now!
Raquel Welch Then & Now! Dawn Wells Then & Now!
Dawn Wells Then & Now!